The worst passwords of 2015 – is yours on the list?
 Weak passwords, using the same one for different websites and unsafe surfing habits can make Singaporeans easy targets for cyber criminals looking to steal private data, cyber security experts here say.
Weak passwords, using the same one for different websites and unsafe surfing habits can make Singaporeans easy targets for cyber criminals looking to steal private data, cyber security experts here say.
Last Monday, a former administrative assistant admitted cracking the passwords of 300 SingPass account holders and selling the details to a China-based syndicate to produce sham Singapore visa applications.
James Sim Guan Liang, 39, made tens of thousands of attempts to guess them when he realized some people used their NRIC number as their SingPass password – which also happened to be their username.
Such targeted attacks are only possible if people choose a word linked to their personal information, which may include things that they share through social media.
“Sometimes the answers to security questions for resetting passwords can easily be retrieved from an individual’s personal data,” said Mr. Vicky Ray, a threat intelligence analyst from network security firm Palo Alto Networks.
“This could be responses to questions like: Where did one go to school? Such information can easily be retrieved from LinkedIn or Facebook.”
It is one of the many ways passwords are cracked by dedicated hackers. Another is by using a weak or common password, like one on the “world’s worst password” list.
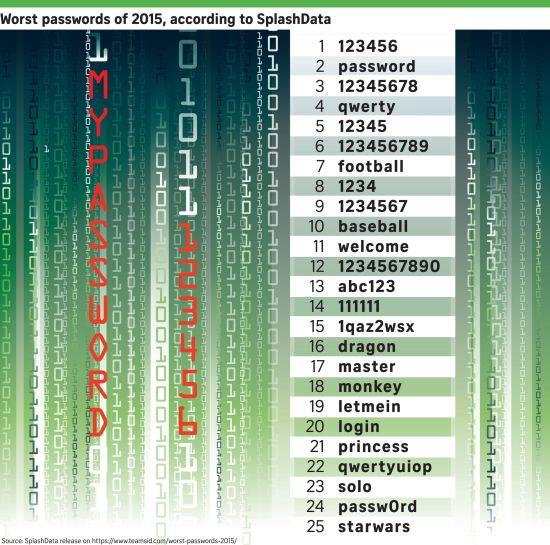
This was published last week by password management firm SplashData, which analyzed more than 20 million passwords globally that were leaked over the last year.
The list was topped by “123456”, “password” and “qwerty” – the first five letters on the top row of a regular keyboard. New entries on the list, now in its fifth year, include pop culture references like “star wars”, “solo”, and “princess”, following the release of the latest Star Wars movie.
Weak passwords are bypassed with software using a “brute force” approach to guessing them.
“With common, widely available cyber security tools, the average six- character, all-lowercase password takes less than 10 minutes to be cracked,” said Mr. David Siah, country general manager of security software firm Trend Micro Singapore. “Adding just one capital letter and an asterisk increases the cracking time for an eight-letter password from 2.4 days to 2.1 centuries.”
Users may also be tricked into giving up their passwords when they surf the Internet.
“Most stolen passwords are ‘lost’ through phishing, where the victim is tricked into voluntarily giving up his credentials to a fake website made to look like the real site,” said senior research fellow Nick FitzGerald from security software maker ESET Asia Pacific.
But Mr. Charles Lim, a senior industry analyst for digital transformation at research firm Frost & Sullivan Asia Pacific, stressed that it is also important for organisations to have strong database security.
Their password database can be hacked into, and the information sold to criminals, he said.
To boost security, passwords should be eight characters or more and include a combination of lower and uppercase letters, digits and symbols. Users should also change passwords often, not use the same password on different sites or use personal information or common words as passwords.
RELATED STORIES
‘Password’ no longer the Internet’s worst password
Russian hackers steal 1.2 billion user names, passwords worldwide














