KickassTorrents clone contains malicious scamming code
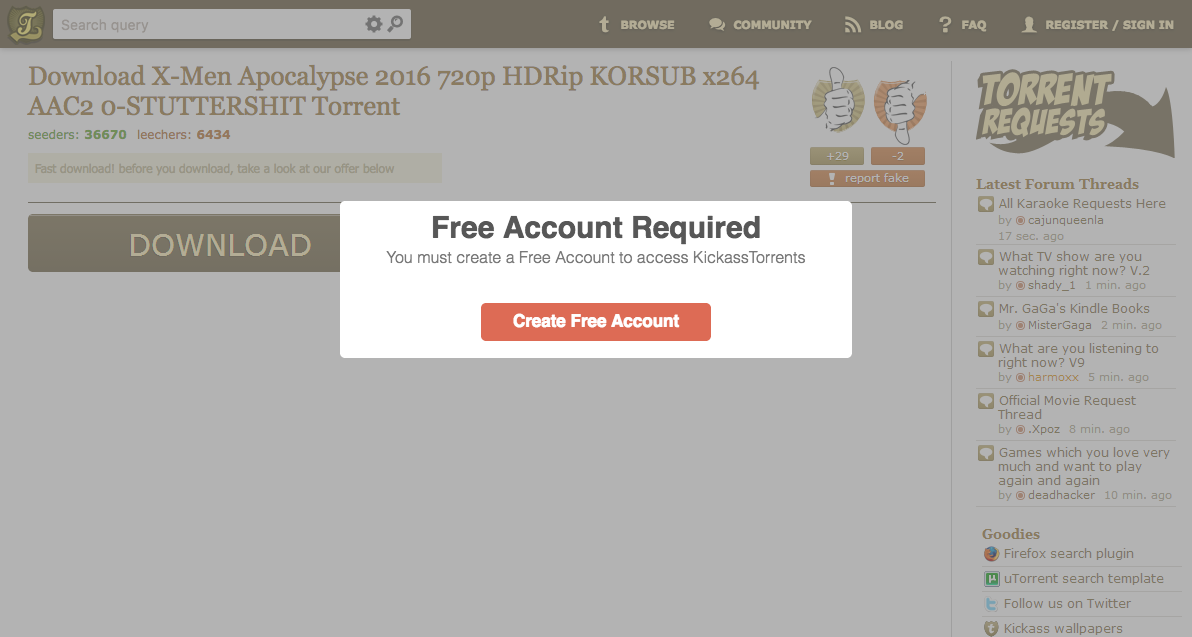
This screen is what will greet users who attempt to download from Kat.am, a KickassTorrents clone. Image Screencapped from KickassTorrets
Clones are popping up one by one to take over and fill the void left by the shutdown of original torrenting sites such as KickassTorrents. However, take heed as it seems that not all clones are created equal.
KAT.am was the first to pop up after KickassTorrents had been taken down but was also put offline shortly after due to a complaint from the Motion Pictures Association, reports TorrentFreak.
When users browsed through the KAT.am site, it appeared to be legitimately serving out torrent links. However, once users clicked on a download link, a new window would pop up with a message stating that a free account was required. The original KickasTorrents site did not require any sort of log-in detail to download torrents.
It would seem that when the .am domain became vacant after the first KickassTorrents clone, KAT.am, was brought offline, scammers got hold of the domain and put up their own mirroring scam site which looked like KAT.am.
This type of “register to download” scam is by no means new but many still fall for this due to ignorance. Don’t be too eager to provide personal details or create a new account if a site requires it to download data. Alfred Bayle














