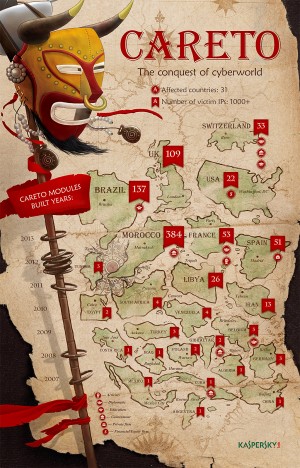
An infographic released by Kaspersky Labs shows the extent the malicious software known as “Careto” has spread throughout the world. Careto attacks and steals vital information from the infected computer for the benefit of its still unidentified creators. CONTRIBUTED IMAGE/Infographics by Kaspersky Labs.
MANILA, Philippines—A computer security software company has discovered a cyber-criminal group believed to be conducting espionage activities through a malicious software, or malware, that has already spread to at least 31 countries.
The malicious software, identified as “Careto,” which is Spanish for “Mask,” is believed to be the most advanced online threat ever seen.
“The Mask is one of the most advanced threats at the current time. This and several other factors make us believe this could be a state-sponsored operation,” Kaspersky Labs said in a report published on its computer security website www.securelist.com.
“We observed a very high degree of professionalism in the operational procedures of the group behind this attack, including monitoring of their infrastructure, shutdown of the operation, avoiding curious eyes through access rules, using wiping instead of deletion for log files, etc. This level of operational security is not normal for cybercriminal groups,” it said.
The authors behind the malware are still unknown but the targets have been identified as primarily government institutions, diplomatic offices and embassies, energy, oil and gas companies, research institutions, private equity firms and activists.
There have been more than 1000 IP addresses infected in 31 countries. The most infections, 383, were seen in Morocco, Kaspersky said.
Brazil had 173 infected IPs, United Kingdom had 109, Spain had 61, France had 52, Switzerland had 33, Libya had 26, while the United States had 22, it said.
“For the victims, an infection with Careto is disastrous. The malware intercepts all the communication channels and collects the most vital information from the infected system,” Kaspersky said.
“Detection is extremely difficult because of stealth rootkit capabilities. In addition to built-in functionalities, the operators of Careto can upload additional modules which can perform any malicious task. Given the nature of the known victims, the impact is potentially very high,” it said.
Careto has been in operations since at least 2007 and could have infected Windows, Apple, Linux, Android operating systems including mobile devices.
“What makes ‘Mask’ special is the complexity of the toolset used by the attackers. This includes extremely sophisticated malware, a rootkit, a bootkit, Mac and Linux versions and possibly versions for Android and iPad/iPhone (Apple iOS),” Kaspersky said.
The way computers were infected was discovered to be through fake emails that contain a link to a malicious website. Sometimes the website would direct to a site imitating a legitimate site.
“Sometimes, the attackers use sub-domains on the exploit websites, to make them seem more legitimate,” Kaspersky said.
“These sub-domains simulate sub-sections of the main newspapers in Spain plus some international ones like the Guardian and the Washington Post,” it said.
RELATED STORIES
Cybercriminals steal info from Facebook, other social media
Global cybercrime ring targeted by Microsoft and FBI