It could have been a scene taken out of a spy movie: one cyber criminal group attacks its targets but unwittingly hits another cyber criminal group who then counterattacks.
The online skirmish between the two groups, who are active mostly in the Southeast Asian region, occurred in March 2014 amid the tragedy of Malaysian Airlines flight MH370.
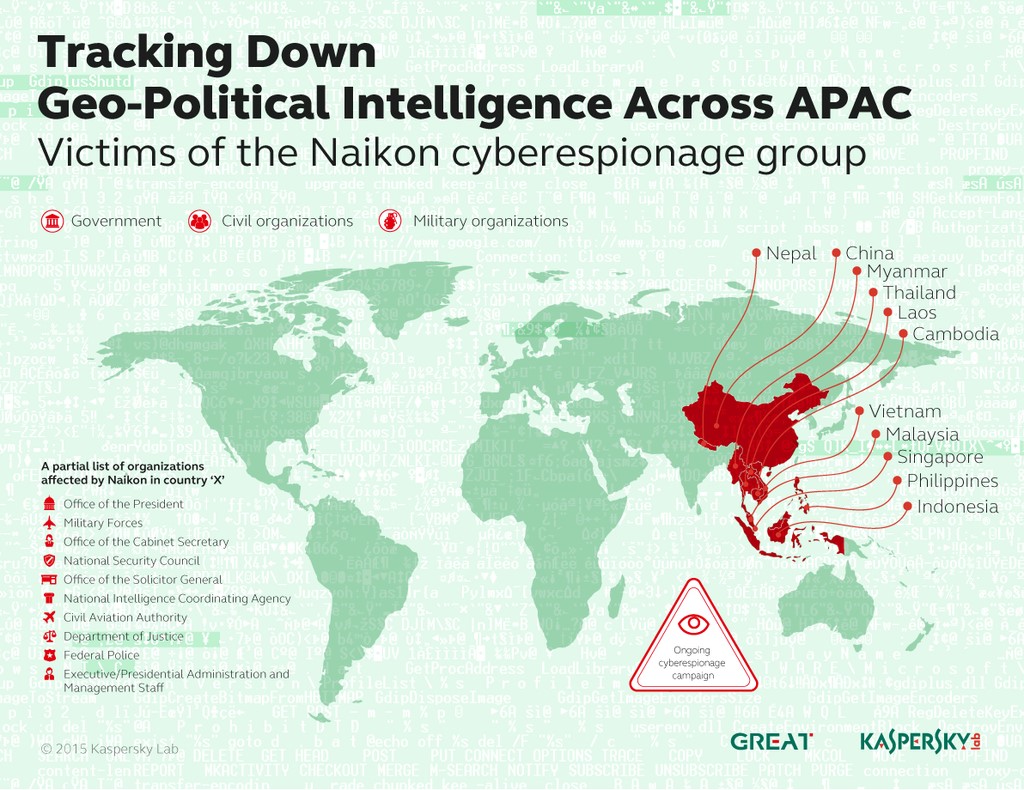
The group who attacked first is called “Naikon” and has a previous record of hitting countries such as the Philippines, Malaysia, Cambodia, Indonesia, Vietnam, Myanmar, Singapore, and Nepal, Kaspersky Labs said in their latest cybersecurity bulletin.
Naikon had sent an email containing a malicious software attachment to an official Malaysian government email address with the intent of gaining unauthorized access to their network and confidential files.
The attack failed when the target did not open the attachment, which was supposed to trigger the malicious software. Instead, the would-be victim tried to validate first if the email was authentic and even retaliated with an email that also contained a malicious software.
READ: 87% of Filipino Internet users have been victims of cybercrimes–DOJ
Vicente Diaz, Principal Security Researcher of the Global Researcher and Analysis Team of Kaspersky Lab, identified the counter attack as coming from the group known as “Hellsing,” and said that this was the first incident of a cyber espionage group retaliating against another.
“That was quite a unique move [which we] don’t see often. However, some groups believe that in case they get attacked, it is legitimate for them to counter-attack. Which obviously is quite a difficult position for all of us, and it will make trouble for everybody,” Diaz said in an interview with INQUIRER.net during the Kaspersky Cybersecurity Summit last April 20, 2015.
Asked if the spy vs spy incident was something akin to a Hollywood blockbuster movie, Diaz said: “Maybe not (as much) action and maybe not so interesting but yes, somehow yes.”
Hellsing, which has been active since 2012, has a previous record of attacking government and diplomatic organizations in the Philippines, Indonesia, Malaysia, and India.
READ: Hackers steal up to $1 billion from banks, security firm says
“In the past, we’ve seen groups accidentally hitting each other while stealing address books from victims and then mass-mailing everyone on each of these lists. But, considering the timing and origin of the attack, the current case seems more likely to be [a group vs group] attack,” the Kaspersky bulletin said.
Government-sponsored cyber espionage groups
Vicente Diaz speaks about the Naikon and Hellsing cyber espionage groups during Kaspersky Cybersecurity summit. Photo by Matikas Santos.
Diaz said that they have reason to believe these cyber espionage groups are sponsored by governments who are looking to get confidential information from their rival countries.
“We were initially suspicious of that [idea] because of the type of targets that they are targeting. Who could be interested in information from one ministry, or from one military organization? Obviously this kind of information could be very useful for some governments,” Diaz said.
He said that these groups would have little use of the information that they gather from governments. What matters was who would be interested to buy the specific information they get.
READ: Cyber security threats to watch out for in 2015
“In the last years, this has become more or less public. A lot of governments are saying they are investing in cyber espionage, they have [hacking] tools [and] they have [hacking] teams and they are doing this all the time,” Diaz said.
“Especially after the [revelations of Edward] Snowden … we have seen that this is really happening, we have the proof now that governments are using this kind of techniques and tools for spying [on] each other,” he added.
The existence of “cyber mercenaries” was also a cause for concern for governments and some companies as they offer their cyber espionage services for a price.
These groups move from country to country, stay for a week or two just to get a specific set of information from a particular target.
READ: Websites need better defense vs growing ‘hacktivism’, says cybersecurity expert
“We believe these groups will be more popular in the future because it is not only governments, but also some companies, who will be interested in doing cyber espionage against [their] competitors so they can gain an advantage,” Diaz said.
Collateral damage?
Asked whether average citizens could be caught in the crossfire when cybercriminal groups attack each other, Diaz said it was possible but only indirectly.
Most likely targets of cyber espionage groups are persons who have access to the network of the target government or company.
The bigger danger, Diaz believes, is when the malicious software used by groups against governments and companies is replicated by others and becomes more common, putting ordinary citizens at risk.
“We have seen this in the past, some cyber espionage campaigns used some malware or some exploits that we have never seen before and shortly after it was discovered, we saw some malicious campaigns from normal cyber attackers using [the same malware or exploit,]” Diaz said.
With the case of Hellsing vs Naikon, he assured that the malware they used have not yet been detected in the Philippines. KS
MORE STORIES:
Globe website hacked due to ‘poor internet connection service’
After Globe, more PH websites hacked