Apple ID passwords may be vulnerable to iOS phishing attacks
INQUIRER.net stock photo
Mobile app developer Felix Krause recently revealed a vulnerability in iOS which may put users’ passwords at risk.
Krause detailed on a personal blog post how attackers could use pop-up dialogue boxes as phishing attacks to trick a user into giving their Apple ID password voluntarily.
Phishing attacks are attempts by hackers to obtain sensitive or personal information through the use of malicious software. Information like passwords, credit card details and more.
Looking at a side-by-side screengrab comparison, there appears to be no difference between the legitimate pop-up and the phishing attack pop-up.
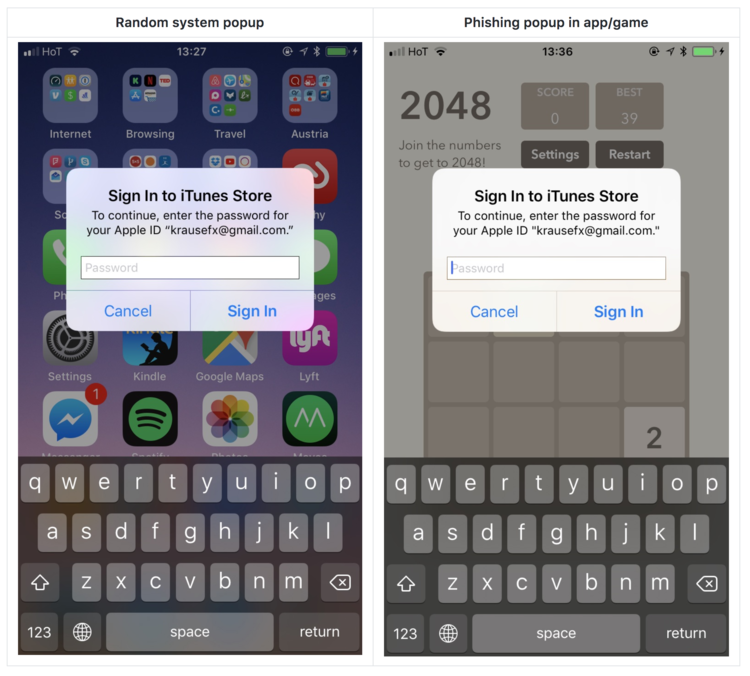
Image: Felix Krause
Krause had created a proof-of-concept app to show the security vulnerability in iOS. He explained that the only way to distinguish the fake pop-up from the real one would be through pressing the “home” button.
Pressing the home button would cause the fake pop-up to close together with whatever app it appeared on. For example, if the fake popup appeared while the user was playing a game, pressing the home button would close the game and the pop-up.
On the other hand, a legitimate system pop-up asking for the user’s password would not close after pressing the home button. He explained that this was because a real system pop-up ran on a different process from a standard app.
Krause also noted that spoofing a system pop-up was relatively easy. It had less than 30 lines of code and every iOS engineer would be more than capable to quickly build their own phishing code.
As for the solution, Krause proposed for app pop-up dialogue boxes to include the app’s icon. This he believes would help identify an app pop-up from a system pop-up, and ultimately a fake pop-up from a real pop-up.
He also recommended that users should use 2-factor verification to increase security. If an attacker got hold of one password, he would have to go through a different security process to complete the attack.
Finally, Krause believes users should not be constantly asked for credentials in the first place to help prevent exploitation of this vulnerability. JB
RELATED STORIES:
iOS 11 Control Center Wi-Fi, Bluetooth shortcuts may be security risk, say experts
iPhone X may earn Samsung more money than Galaxy S8 — report