Apple offers workaround to MacOS High Sierra root login security bug

Image: INQUIRER.net Stock Photo
The discovery of a major security flaw in Apple’s latest MacOS High Sierra has put many users on high alert. The company quickly responded to the reports with a workaround to prevent unwanted access to Mac computers while they work on a patch.
This security bug allows anyone full access to a Mac running on High Sierra version 10.13.1 (17B48) by simply typing “root” on the User Name portion of the log-in window.
Fortunately for other Mac users, the bug does not affect older versions of MacOS.
According to TechCrunch, Apple quickly issued a statement acknowledging the issue. It also provided a step-by-step guide to turn off root login or apply a password until an update to fix the bug could be released.
Founder of Software Craftsman Turkey Lemi Orhan Ergin first made the issue publicly known through a tweet. He tagged both Apple Support and the main Apple Twitter account to quickly get feedback.
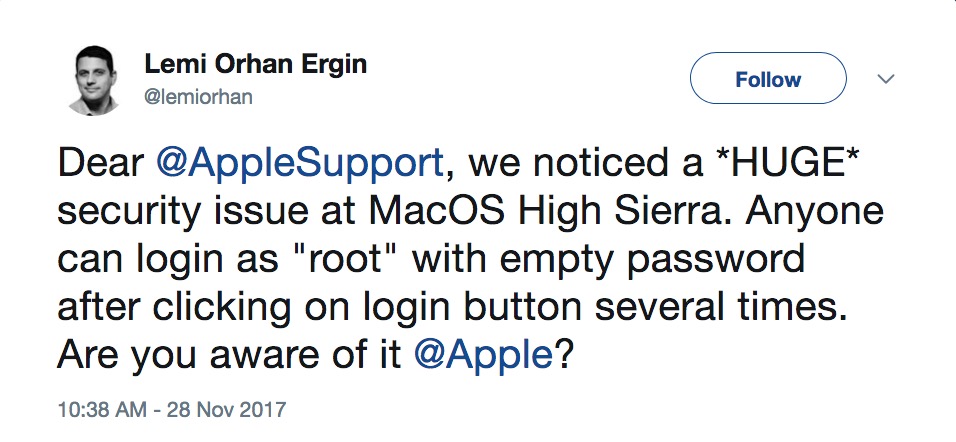
Image: Twitter/@lemiorhan
For the time being, it would be advisable to not leave Macs running on High Sierra unattended. Alfred Bayle /ra
RELATED STORIES:
Apple ID passwords may be vulnerable to iOS phishing attacks
‘Thoughts of suicide’ to be detected by AI in Facebook posts
iPhone X ‘notch’ remover now downloadable from App Store