Chinese hackers stealing digital info from PH gov’t agencies
Has China been hacking into computers of Philippine government and military organizations and stealing sensitive information for the past years?
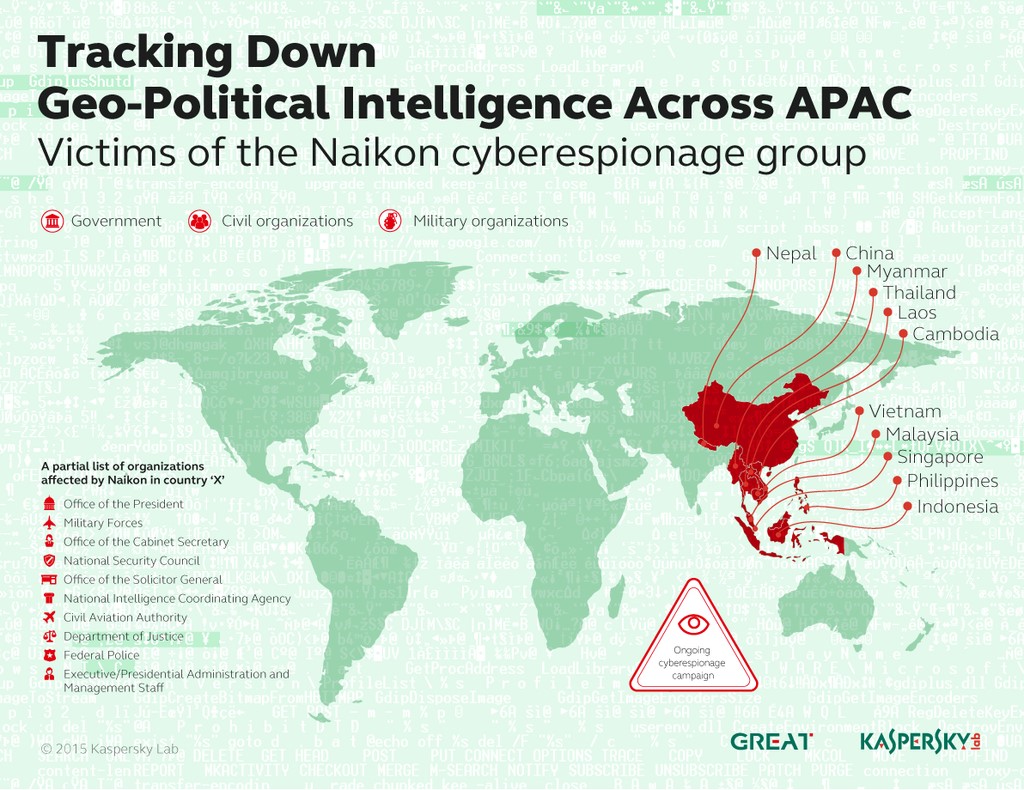
Computer security firm Kaspersky Labs said in their latest cybersecurity bulletin that a Chinese-speaking hacker group called “Naikon” had successfully infiltrated governments around the South China Sea region including the Philippines.
Naikon had been conducting “at least five years of high volume, high profile, geopolitical attack activity” and had a “high success rate in infiltrating national organizations in Asean countries,” Kaspersky said.
READ: Spy vs spy: Two cyberespionage groups engage in online skirmish
“In the spring of 2014, we noticed an increase in the volume of attack activity by the Naikon [group]. The attackers appeared to be Chinese-speaking and targeted mainly top-level government agencies and civil and military organizations in countries such as the Philippines, Malaysia, Cambodia, Indonesia, Vietnam, Myanmar, Singapore, Nepal, Thailand, Laos and China,” Kaspersky said in their security bulletin posted on securelist.com
“An attack typically starts with an email carrying an attachment that contains information of interest to the potential victim. The document may be based on information from open sources or on proprietary information stolen from other compromised systems,” Kaspersky principal security researcher Kurt Baumgartner said in the bulletin.
Once the victim opens the attachment, a spyware program is installed on the computer without the victim’s knowledge. A decoy document will open to make the victim think nothing suspicious happened.
The spyware program is capable of getting information from the victim’s computer and sending it back to the hacker.
READ: 87% of Filipino Internet users have been victims of cybercrimes–DOJ
“There are 48 commands in the module’s repertoire, which a remote operator can use to effectively control the victim computer,” Baumgartner said.
“This includes taking a complete inventory, downloading and uploading data, installing add-on modules, or working with the command line.” he said.
Gov’t agencies hit in ‘Country X’
Kaspersky Labs provided an example of the how deep Naikon can infiltrate a government’s computer systems using “Country X.”
“Analysis revealed that the cyberespionage campaign against Country X had been going on for many years. Computers infected with the remote control modules provided attackers with access to employees’ corporate email and internal resources and access to personal and corporate email content hosted on external services,” Baumgartner said.
“A few of these organizations were key targets and under continuous, real-time monitoring,” Baumgartner said.
• Office of the President • Military Forces • Office of the Cabinet Secretary • National Security Council • Office of the Solicitor General • Intelligence Services • Civil Aviation Authority • Department of Justice • Federal Police • Executive/Presidential Administration and Management Staff
Kaspersky did not explicitly state which country in Southeast Asia is Country X.
State-sponsored cyberespionage
Kaspersky believes Naikon is among the many state-sponsored cyberespionage groups looking to steal information from other governments.
READ: Hacker targets info on MH370 probe
Their highly sophisticated hacking methods and well-organized attacks against government agencies are not something that a single hacker would be able to do, Vicente Diaz, principal security researcher of the global research and analysis team of Kaspersky Labs, said in a previous interview.
“We were initially suspicious of that [idea] because of the type of targets that they are targeting. Who could be interested in information from one ministry, or from one military organization? Obviously this kind of information could be very useful for some governments,” Diaz said.
“In the last years, this has become more or less public. A lot of governments are saying they are investing in cyberespionage, they have [hacking] tools [and] they have [hacking] teams and they are doing this all the time,” Diaz said.
West Philippine Sea maritime dispute
China is involved in a maritime dispute with neighboring countries, namely Philippines and Vietnam, over its nine-dash claim that covers nearly the entire South China Sea including parts of the Spratly Group of Islands.
Philippines has already filed an arbitration case against China in the International Tribunal on the Law of the Sea. China has refused to participate in the proceedings insisting it has undisputed sovereignty in the region.
China has started reclamation projects in several reefs in the Spratly Islands off the coast of Palawan despite strong protests from the Philippine government.
RELATED STORIES
Filipino hackers fight back, deface Chinese sites
Chinese websites hacked over poaching, Spratlys reclamation