Cyberespionage group that hit PH and Southeast Asia ‘disappears’
From 2009 up to 2015, a single group of people has successfully hacked into computers of various government agencies of Southeast Asian countries and steal data without being caught.
But in May 2015, the cyberespionage group dubbed “Naikon” suddenly disappeared after their operations were exposed in a public report by computer security firm Kaspersky Lab.
“This was a bit of a surprise because it was such a long-running and large effort and all of a sudden it disappeared,” Kurt Baumgartner, Kaspersky Principal Security Researcher, told INQUIRER.net in an interview during the recent 2016 Security Analysts Summit in Tenerife, Spain.
Baumgartner investigated and co-wrote the report that exposed the workings of the Naikon cyberespionage group and he was able to track the group’s activity until it retreated back into the shadows.
READ: Chinese hackers stealing digital info from PH gov’t agencies
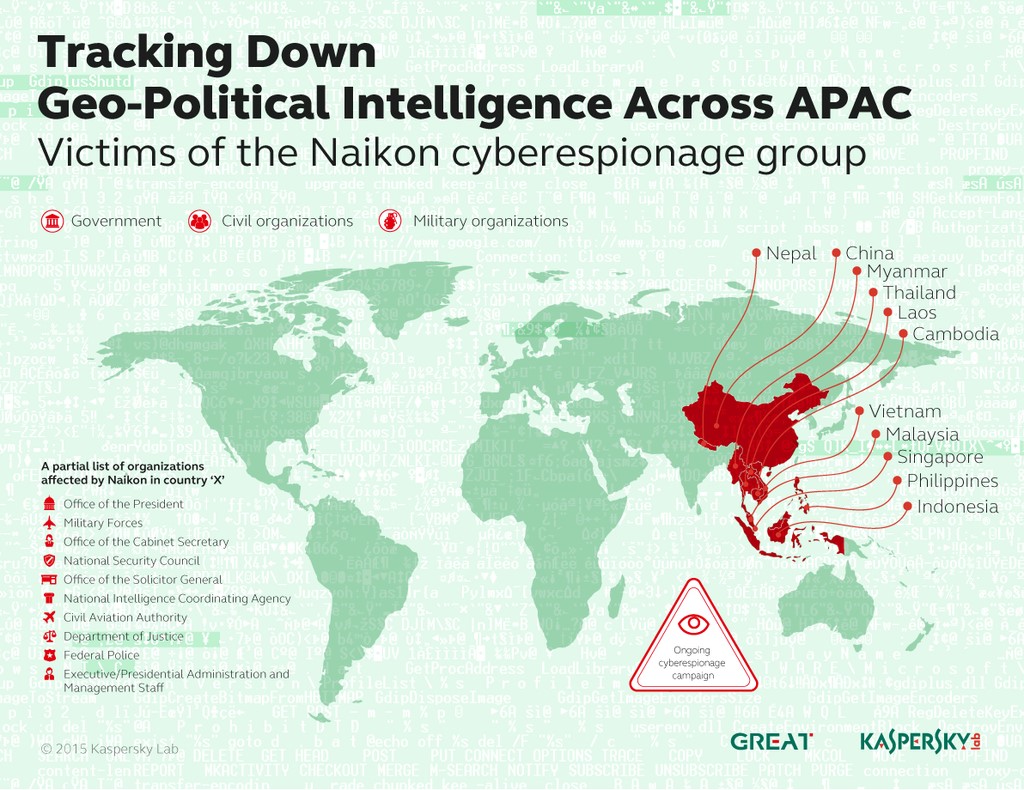
Victims involved in South China Sea dispute
The primary targets of Naikon’s cyberespionage campaign were Southeast Asian countries located around the South China Sea including the Philippines.
Baumgartner said that the group collected data and intellectual property from government agencies who have information related to geopolitical issues through “spear phishing” attacks.
Spear phishing is a method used by hackers to get access into a target’s computer. It is done through emails with an attachment that looks like an ordinary document. The email is deliberately made to look like a message from a colleague or an acquaintance to trick the target into downloading the attachment.
Kaspersky did not name outright who they suspect Naikon could be but Baumgartner noted that “there are Chinese-speaking artifacts in that malware” left by those who developed the hacking tools
The attached file is actually a program that would allow the hacker to access the computer without the victim’s knowledge. Files like these are called “malicious software” or “malware.”
“With their spear phishing, we saw these guys focus on a particular theme or topic and it was headline news of some sort and it was geopolitically related so it seemed like campaigns were focused according to certain themes,” Baumgartner said.
The filename of one particular attachment mentioned Johnson Reef, also known as Mabini Reef, in the disputed West Philippine Sea.
The maritime dispute over the South China Sea has been a big issue for many countries in Southeast Asia and Baumgartner mentioned this has been used by cybercriminals as bait in their spear phishing attacks against government agencies.
READ: China says it sent ships to disputed atoll in West Philippine Sea
Philippines is a major player in the dispute against China which has an all-encompassing claim in the South China Sea including parts of the West Philippines Sea. The arbitration case before the international arbitral tribunal is set to give its award after around two years of hearings.
“There were a number of different topics and themes. When it came to the Philippines, themes that were related had to do with maybe the Johnson reef. There was a center on the Philippines related to some long-term projects with some western governments. I think all of those were used as themes,” Baumgartner said.
Exfiltration of data
After years of accessing the computers of their targets and obtaining data, Naikon suddenly stopped all operations and dismantled its network when Kaspersky released its report in May 2015.
Baumgartner said he tracked a massive movement of data across Naikon’s network of servers including the pulling out of data after they were exposed by Kaspersky.
READ: Spy vs spy: two cyber espionage groups engage in online skirmish
“The data that may have been collected before is only useful for so long … the desire for that information will still be there and the efforts that have been going into collecting that data will simply be shifted to join other projects or for a new set of attacks,” Baumgartner said.
He added that Kaspersky has already cleaned up the infected computers of victims so that Naikon will no longer be able to access these.
“Where there were infections. Those infections have been cleaned up … and I think that it has been pretty successful,” he said.
Kaspersky did not name outright who they suspect Naikon could be but Baumgartner noted that “there are Chinese-speaking artifacts in that malware” left by those who developed the hacking tools.
A sample of a hacking tool used by the Naikon cyberespionage group that successfully hacked government networks in Southeast Asia.
Fragmented security landscape
Across Southeast Asia, cybersecurity is seen as very fragmented, according to Vicente Diaz, Kaspersky Security Research Analyst.
“Different countries have very different levels of security awareness and implementation of best security practices. There are big companies they are mature enough to know they might be the target of these attacks especially banks or all these companies that might suffer financial losses,” Diaz said in a separate interview with INQUIRER.net.
Vicente Diaz Kaspersky Cybersecurity analyst speaks about the Naikon cyberespionage campaign in a media event in Manila.
“Unfortunately, many times we see that people are running pirated software and the computers are not updated, so they have more chances of becoming infected. In the end this might become big trouble because they might be attacked by financial malware or their data is stolen,” he said.
Asia accounts for nearly half of the global total of internet users according to November 2015 figures from www.internetworldstats.com. In Southeast Asia, Indonesia has the highest population of users with 78 million followed by Vietnam and Philippines which both have around 47 million.
“But we see a lot of potential we see a lot of people bringing a lot of energy very smart guys working in this industry right now. This is encouraging. I believe in the future this situation will change quite radically,” Diaz said. CDG